Hardware Wallet Security Concerns
And How Ethos Addresses Them With Magic Key Technology

Introduction
In the rapidly evolving landscape of blockchain technology, security is paramount. New attention has been turning to the crypto hardware wallet space, as Ledger recently discovered when it offered a new key recovery service for its popular Nano wallet.
People started to realize that hardware wallets didn’t function the way they thought they did, and worry about what they didn’t know. These worries primarily center around the firmware exporting keys from the device’s “secure element” (SE), and the introduction of a new attack surface due to Ledger’s proposed backup and recovery system.
At Ethos we’ve thought a lot about crypto key security, sharding, backup and restoration. This article will shed some light on these issues, illustrating why a typical hardware wallet firmware might not be as concerning as it first appears, and why the real concerns might lie in the security model of the types of services proposed by Ledger.
Firmware Exporting Keys
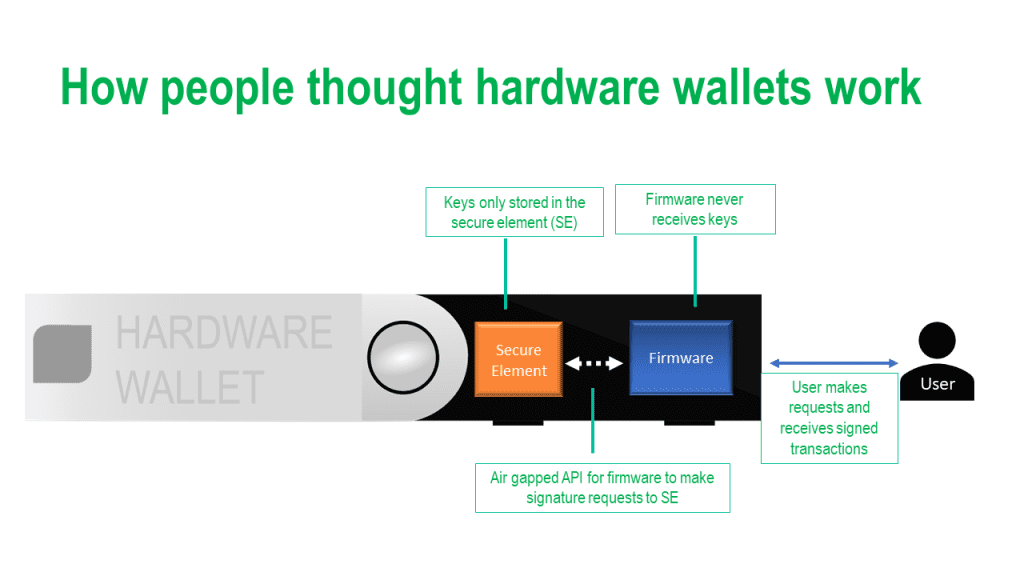
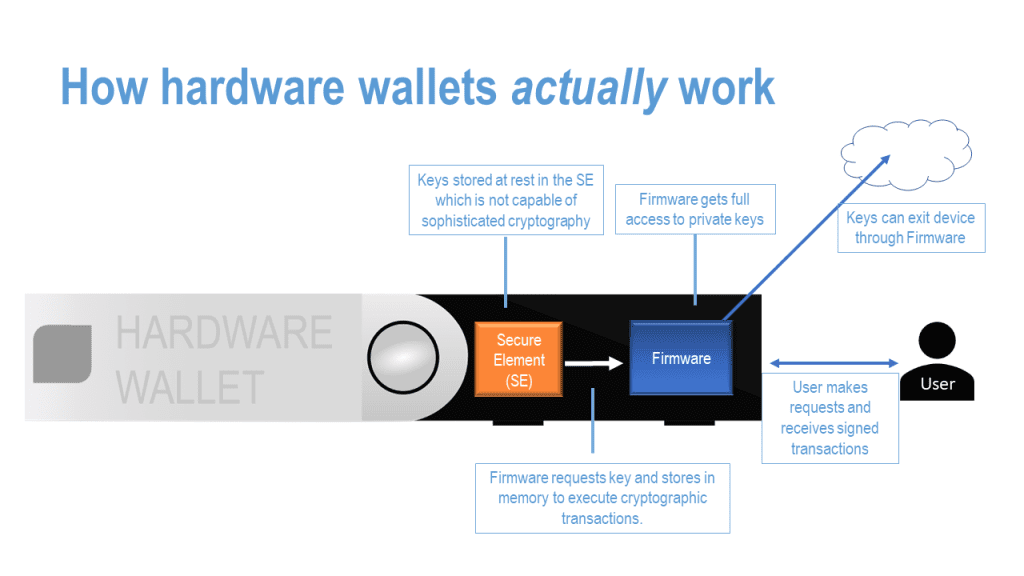
A major point of concern for many in the Ledger situation has been the fact that the firmware has full access to keys from the device’s secure element (“SE”). The SE is a specialized piece of hardware that stores and manages private keys. Many users assumed that their private crypto keys never left the SE. While the news that private keys leave the SE was initially alarming to many, it’s important to understand why it is implemented in this way. The SE, while secure, can only perform a limited set of cryptographic functions. This is an issue when working with diverse blockchain protocols, each requiring their own unique functions.
Furthermore, blockchain protocols are continuously evolving and improving. Trying to keep the SE updated to cater to these changes would be practically impossible, and would result in hardware that rapidly becomes obsolete as technology progresses. Instead, Ledger’s firmware exports the keys, performs the necessary cryptographic functions, and then clears the keys from memory. This way, the SE doesn’t need to be constantly updated, users can receive firmware updates rather than hardware updates, and the hardware retains its relevance and usability.
In most hardware solutions, trusting the firmware is a necessity. It’s unrealistic to expect a seamless user experience without this level of trust. The important assumption here is that the keys won’t leave the hardware/firmware layer, thus maintaining an air gap between the hardware device and the outside world. This forms the crux of the device’s security.
New Attack Surfaces
While concerns around firmware and key exports may be somewhat misunderstood, the kind of backup system proposed by Ledger introduces new, potentially more concerning attack surfaces. This system involves creating three shards of the user’s keys and storing them with centralized custodians. The key can be reconstructed from any two of these three shards.
The problem arises from the fact that these custodians are centralized. If they are compromised—either through a cyberattack or by a government entity legally compelling them to surrender the shards—the user’s private key could be reconstructed without their knowledge or consent. This effectively breaks the core security assumption that the full copy of the key only ever exists on the user’s own device.
This shift in attack surface from the hardware device to potentially less secure centralized custodians is a significant concern. It introduces new vulnerabilities that users must consider when choosing how to secure their cryptocurrencies.
Decentralized Backup Solutions
One major issue Ledger’s system attempts to resolve is the problem of “key anxiety”. This refers to the worry users experience around managing and storing their keys securely, a task that often proves too complex or burdensome for many casual users. This issue has led many to opt for centralized custodians or other less secure services, both of which present their own set of risks.
However, it is imperative that solutions to key anxiety do not sacrifice the fundamental principles of decentralization and security. Introducing centralized vulnerabilities undermines the core philosophy of blockchain technology. Ideally, the user should be the only one able to initiate and restore keys, and the full copy of the key should always be in the user’s possession, never leaving the hardware or software layer they are using.
Allowing parties other than the user to restore keys introduces a new level of centralization risk and potential security vulnerabilities. In other words, while the convenience of centralized custodians might be tempting, it does come at a cost to user control and security.
How Ethos Magic Keys Work
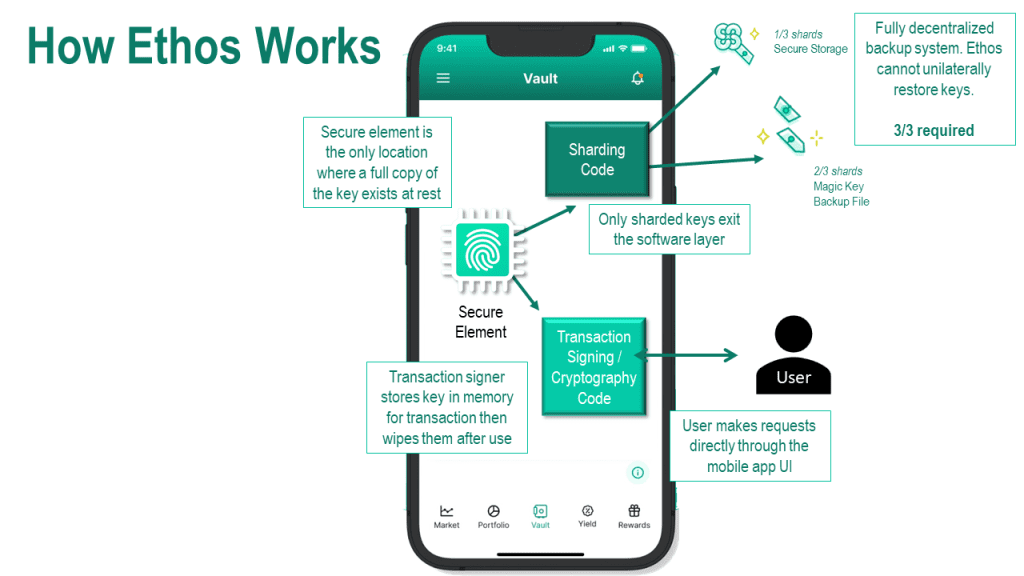
Recognizing these challenges, at Ethos, we’ve developed a solution that aims to resolve key anxiety without compromising on decentralization and security. Our patent-pending solution, called Magic Keys, is a fully decentralized key backup and restoration service.
With Magic Keys, the full copy of the key only ever exists on the user’s device, stored securely within the device’s SE—TEE on Android and Secure Enclave on iPhone. Ethos cannot unilaterally restore users’ keys. Only the user can restore their own keys.
We’ve also introduced a layer of social guardians, a feature designed to add an additional security layer without increasing the attack surface. This system allows users to nominate trusted individuals who can help in the restoration process, yet without any one of them ever having access to the user’s full key.
If you want to learn more about Magic Keys, you can learn more about our innovative solution here.
Conclusion
The Ledger situation serves as a crucial lesson about the importance of decentralization, security, and clear communication in the world of blockchain. While efforts to alleviate “key anxiety” are necessary, solutions should not compromise on these critical aspects. Ledger has been on a listening tour to understand user’s concerns and are considering changes to how they approach their key backup technology.
Ethos aims to address these concerns with Magic Keys, a fully decentralized backup and restoration system that ensures the user remains in control. We believe this represents a major step forward in empowering users while maintaining a robust security protocol.
As we navigate the ever-evolving landscape of blockchain technology, it’s important to remember that while convenience is desirable, it should not come at the cost of security and user control. Always prioritize a solution that maintains your autonomy and the security of your digital assets.
