Meet The World’s Most Secure Crypto Self-Custody Device: Your Mobile Phone

By Adam Lavine
The Secret Powerhouse in your Pocket
You probably have access to an extremely powerful secret weapon for storing your crypto: your mobile phone.
All you need is the right software and platform.
Hardware Wallets–Secure, But Not Without Risks
Many people think hardware wallets are the most secure device to store crypto, and inarguably they are highly secure. But they are not without their risks and disadvantages. When we (re)started Ethos we wanted to build the world’s best Defi platform, and that doesn’t happen without top-tier, secure key storage at the core of the solution.
Most people think a hardware wallet stores your crypto. In fact, your crypto is “stored” on the Blockchain, secured by your private cryptographic keys. Hardware wallets only stores your keys and limits access via an air-gapped USB drive secured by a PIN There are risks and downsides to this approach, which we will cover later. First, let’s introduce you to a powerful hardware storage solution that you may already have in your pocket.
The Crypto Industry needs a Mainstream Self-Custody Solution
In the wake of the meltdowns of FTX, Voyager and Celsius, the Ethos team saw the immediate need for a consumer-friendly, robust and free enterprise grade self-custody solution. Centralized exchanges can be convenient when they work, but customers learned hard lessons in 2022 that the crypto they stored on centralized exchanges did not legally belong to them. They were unsecured creditors of the exchanges – meaning the exchange owed them the crypto in their accounts and most likely wouldn’t get it all back in the event of a bankruptcy.
The alternative to an account on an exchange is for the crypto investor to take responsibility for storing crypto themselves through a private key, seed phrase and hardware wallet. This obviously works but puts a heavy technical and security burden on ordinary people. If you lose your device and your key or if your key is stolen your crypto can be lost or stolen. In fact, many people are flabbergasted to learn that even if your keys are stored on a hardware wallet your crypto is at risk if someone gets access to your keys. If someone gets access to your keys, it doesn’t matter how secure your wallet is. The wallet is just a method of securing the key but doesn’t prevent other people from using it.
Free, Easy and Secure Self-Custody for All
We believe self-custody is critical for crypto to be truly useful and secure for everyone. So we took the Ethos team’s collective 50 years of experience building cryptographic software, self-custody and trading platforms and challenged ourselves to build a solution that was easy and secure. Building the solution with a mobile-first consumer-friendly app as the front-end – with a highly secure crypto Vault at the core – was a no-brainer.
This article will cover a brief history of mobile cryptographic hardware, and how the design is actually perfect for securing private keys in a method that is arguably more secure than a hardware wallet. Best of all – assuming you have the right model of phone (and you likely do) – then it’s free! No need to purchase extra hardware to have the security of storing your own private keys and crypto.
Mobile Phones Have Replaced Many Devices – Is the Hardware Wallet Next?
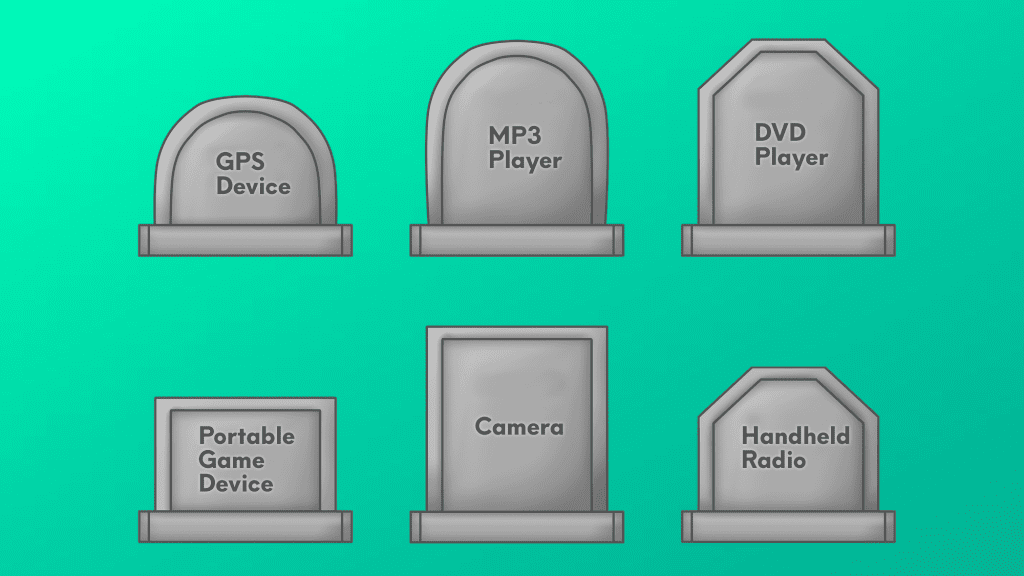
Mobile devices, starting with the iPhone, disrupted many devices and media markets including:
- Mobile Software, by allowing developers to easily create and distribute their own apps
- The personal music player market, as the device’s built-in iPod and music streaming capabilities made dedicated music players less necessary.
- Digital cameras, which dropped from 120 million units per year to 9 million units per year over the 10 years following the release of the iPhone
- smaller markets such as flashlights, alarm clocks, timers and watches
This gave rise to new mobile first companies that disrupted entrenched old-tech businesses — Uber displaced taxis, Airbnb displaced hotels and travel agents, Doordash displaced takeout food, among many others.
Of course the mobile device alone is not enough to ensure success; that requires a business model that offers a better solution to a clear consumer need. We see that need in hardware wallets for crypto. It’s a perfect use case for mobile devices because of one more innovative and trailblazing technology yet lesser known technology Apple first introduced: the Secure Enclave.
Secure Enclave: Designed for Maximum Security
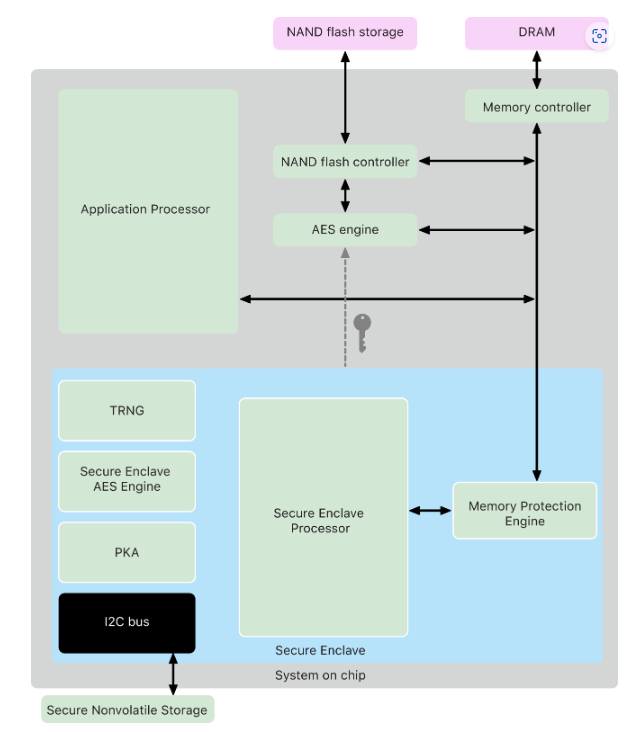
Apple’s Secure Enclave was first introduced as part of the iPhone 5s in 2013 with the A7 chipset. The Secure Enclave is a specialized dedicated secure subsystem that is integrated into Apple systems on chip (SoCs). It was designed to protect sensitive data on Apple devices, initially fingerprints and encryption keys. Its capabilities expanded into handling Touch ID and Face ID, as well as the encryption of user data on the device. It also plays a role in the security of Apple Pay and other financial transactions.
The Secure Enclave is isolated from the main processor to provide an extra layer of security and is designed to keep sensitive user data secure even when the Application Processor kernel becomes compromised. It follows the same design principles as the SoC does—a boot ROM to establish a hardware root of trust, an AES engine for efficient and secure cryptographic operations, and protected memory. Although the Secure Enclave doesn’t include storage, it has a mechanism to store information securely on attached storage separate from the NAND flash storage that’s used by the Application Processor and operating system.
Apple’s Secure Enclave and the U.S. Government

Apple even clashed with the FBI, who wanted to access data stored on the Secure Enclave. In an open Customer Letter, Apple took the unusually strong position of refusing to modify their system code to enable access to the Secure Enclave. By making these requests of Apple, the U.S. Government essentially conceded that Apple’s current implementation of Secure Enclave is unhackable.
Apple’s Secure Enclave Improvements Since Launch

Apple expanded the Secure Enclave’s capabilities to enable features such as Touch ID and Face ID, which allow users to quickly and easily unlock their device and make payments using their fingerprints or facial recognition. This was highly convenient for users, as they no longer had to remember complex passwords or carry around separate hardware devices to access their sensitive information. The secure enclave also enabled integration with other services such as Apple Pay and third-party apps that also use the secure enclave for storing sensitive information. This third-party app integration is what Ethos is using to secure private keys.
The Secure Enclave is completely isolated from the iOS. For example, when you enter a passcode, fingerprint, Face ID or Touch ID, the iOS has no idea whether it is correct. It instead passes the data to the Secure Enclave which checks it against the encrypted version stored there and passes back a simple Boolean Yes/No. In other words, the verification occurs within the Secure Enclave and the only communication with the iOS is a simple OK or not.
In later models, the Secure Enclave was integrated into the A-series SoC (System on Chip) and its security capabilities were further improved to include features such as Secure boot chain, Secure Firmware updates and Secure boot for apps. The Secure Enclave is considered to be one of the most secure mobile security solutions available on the planet, and has played a key role in Apple’s services. In fact, the Ethos team considered Secure Enclave as part of their strategic model of providing extremely secure self-custody with layered services around it (more on that later) .
Android Follows with the Trusted Execution Environment (TEE)

Android followed in the wake of Apple’s Secure Enclave with its Trusted Execution Environment (TEE). Similar to Apple’s Secure Enclave, TEE is a secure area of a mobile device’s processor that ensures sensitive information, such as payment and biometric data, is protected from potential security threats. TEE allows for sensitive information to be processed and stored separately from the main operating system, making it more difficult for attackers to access. The TEE is implemented in the ARM Cortex-A processor, which is found in most mobile devices.
TEE is supported on a wide range of Android devices. Roughly 89% of Android devices now support TEE, supported through the ARM Cortex-A processor family. Popular Android devices that support TEE include the Samsung Galaxy S Series, Samsung Galaxy Note Series, Google Pixel Series, OnePlus Series, LG G Series, among many others.
.
Benefits of using the Secure Enclave and TEE

Storing private keys on the secure hardware of Apple and Android mobile devices provides several benefits for users.
First and foremost, it improves security. Because the secure enclave is a hardware-based security feature that is isolated from the main processor and operating system, the private keys stored in the secure enclave are protected from software-based attacks, such as malware or hacking attempts. Additionally, the secure enclave uses biometric authentication, such as fingerprint or facial recognition, to ensure that only the authorized user can access the private keys.
Second, it enhances convenience. Storing private keys on a mobile device means that users can access them anywhere, at any time vs. a hardware wallet that tends to be left at home or in a safe. This is particularly useful for individuals who frequently use decentralized apps (dApps) or blockchain-based services, as they can easily sign transactions or access their digital assets without having to rely on a separate hardware wallet or other device.
Third, it enables better integration with other services. By storing private keys on a mobile device, users can easily connect to decentralized exchanges, wallets, and other blockchain-based services. This allows for a seamless and streamlined user experience.
In conclusion, storing private keys on the secure enclave of mobile devices provides improved security, convenience, and integration with other services. It is a secure and practical way to store digital assets and private information.
The Risks of Hardware Wallets

According to Blockchain security firm Halborn, risks associated with crypto hardware wallets, including:
- Physical Security Threats: Because hardware wallets are physical, they can be lost, stolen or damaged. Additionally physical access can enable potential tampering to access private keys. The Secure Enclave and TEE protect against this to some extent with tamper-resistant technology.
- Power Glitching: A “fault-injected attack” would seek to create errors to disrupt a hardware wallet’s normal behavior by manipulating voltage modulation, which could force a wallet to behave abnormally and grant access to the recovery seed.
- Firmware Risks: An attacker could potentially modify the firmware on a hardware wallet, enabling them to extract a user’s private keys.
- Side-Channel Attacks: These types of attacks exploit the physical characteristics of a device to obtain otherwise inaccessible information. For example, electromagnetic emissions could infer data being processed by a device. Side-channel attacks have been used to extract crypto keys from hardware wallets.
- Social engineering dangers: Even with strong protection, private keys can be extracted through phishing or other methods. One unlucky consumer even purchased a hardware wallet on eBay that included a “pre-installed key.” The hacker just waited a couple of months, and then used the same private key to drain the funds from the “secure” hardware wallet that used that key.
There’s also the simple risk of losing or exposing your keys and your hardware wallet.
Halborn has a good blog article on the risks of hardware wallets that is worth reading for anyone who owns a hardware wallet.
The Ethos Universal Vault : Transforming Your Mobile Device into a Hardware Wallet

When we set about building the next-generation Ethos Vault, we challenged ourselves to create an extremely powerful, secure and easy-to-use system. We naturally felt the best strategy was to create a mobile-first solution that leveraged Apple’s Secure Enclave’s and Android’s TEE.
The very nature of a mobile device makes it an excellent hardware wallet if the software is properly implemented. This disclaimer is extremely important: there are many mobile wallets on the market that do an inadequate job of securing a user’s private keys, providing backup and restore and enabling features such as social guardians.
But if the mobile app is well-engineered, mobile devices with Secure Enclaves offer military-grade security protection. These characteristics include:
- Highly secure dedicated secure enclave
- Bio-authentication required to access
- A device that is always with the user, making theft less likely
- Native app-only access layer that substantially reduces attack surface
The bio-authentication alone is a major feature that makes the mobile device a very secure option. The chances that a hacker has access to your face, fingerprint or iris is fairly low, and these bio-authentication features are completely absent on most hardware wallets.
In addition, we layered other security features on top of the Universal Vault, including:
- Key Sharding: Letting users shard their keys into multiple fragments
- Key Backup aka “Magic Keys” : Being able to encrypt shards with safe words and back them up on services like Apple Cloud and Google Drive.
- Key Restoration: A robust key restoration process that uses only 2 shards and “safe words” enabling users to recover their keys in case the device is lost.
- Social Guardians: Being able to add trusted email addresses of individuals who can “veto” any key recovery process.
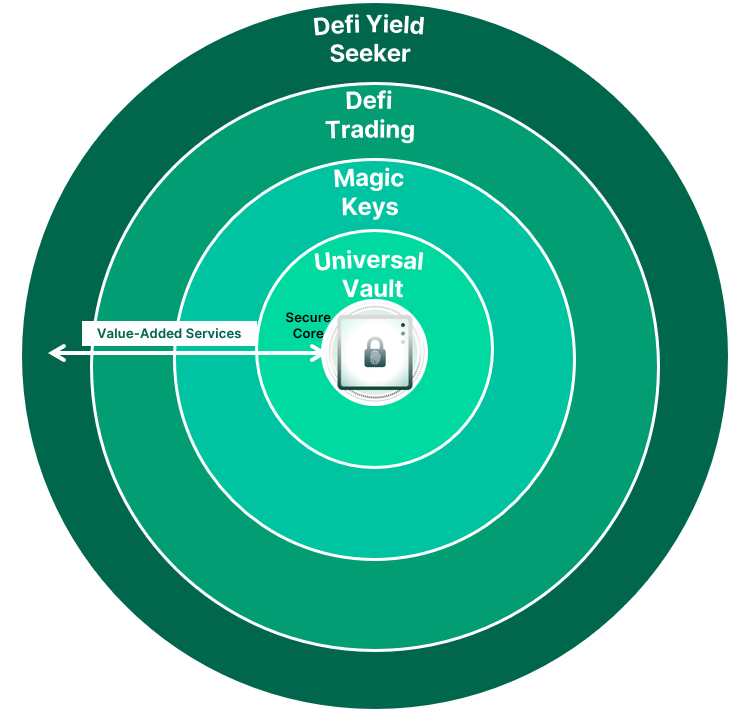
Ethos Technical Architecture
Ethos put the Universal Vault at the core of its services. We felt that we needed this a highly secure self-custody solution at the core of our solution. This was driven by a philosophy that crypto is intended to empower individual control and self-sovereignty, not trusting centralized exchanges that may not be ethical, competent or solvent.
The next layer outside of Universal Vault are the Magic Keys, a patent-pending method to shard, encrypt, backup and restore a user’s keys. This method safeguards the user against device loss as well as theft with a social guardian feature that enables select email addresses to “veto” a transaction. Magic Keys still require the user to take responsibility for their own security, but gives extremely powerful tools for user’s to take responsibility for their own crypto keys.
Once we solved these two core elements, our plan is to add Defi services to the mix. Defi Trading uses a best price discovery engine to compare prices across dozens of defi crypto protocols. It uses established protocol pathways, giving users new prices with an 8 second tick (the block counter tick for Ethereum 2.0)
The outer layer is Defi Yield Seeker, a way for users to setup their own Defi Yield strategies, or look at strategies created by others.
DeFi User Flow
In all of these services, the unifying theme is self-custody and self-directed trades. At no time in this architecture does Ethos ever take possession of keys or assets. Everything always remains 100% under individual user control, and all trades are settled on chain. Price discovery is transparent, with a nominal software licensing fee applied to use the software. (This fee can be lowered if the user holds ETHOS tokens)
This diagram shows how all of these elements come together. A user’s keys are stored on the secure enclave, and can be further sharded, encrypted and backed up to safeguard against device loss. The user accesses protocols directly through their device live on chain, and personally signs transactions using their fingerprint as a biomarker on their mobile device.
In this way, the device is performing three important functions for the end user:
- Secure key storage using the secure enclave
- A Defi “browser” to view and execute trade and yield transactions
- Transaction signing and authentication
Envisioning a Future that is Open, Safe and Fair for All

Moving forward, we believe the networked community of individuals who own their own assets and can choose to deploy them in any manner they wish holds tremendous potential. With the advent of dollar-backed stablecoins such as Circle’s USDC, smart contracts can be deployed that can leverage the potential of the Blockchain without the risk of asset price volatility. Borderless transactions of a diversity of risk and asset flavors becomes possible with instant settlement and transparent on-chain transaction histories. Systems like Ethos can enable anyone in the world with a compatible mobile device to safely and securely participate. By decentralizing asset control, faithless custodians like FTX, Voyager and Celsius will not be able to expose customers to undisclosed risks or deploy assets without their permission.
We are excited about this future, and hope you join us in making it a reality.
